
Share
By Ragavan
 Feb 2023
Feb 2023
 3 Min Read
3 Min Read
How to Prevent Unauthorized Access: 7 Effective Strategies
What is Unauthorized Access?
“Unauthorized access” is unauthenticated users having access to an organization’s data, networks, endpoints, programs, or devices, without its permission. It is carefully associated with authentication – a system that verifies a user when they are in the system. Broken, or misconfigured authentication are the cause for unauthorized parties.
Risks of Unauthorized Access
Once a malicious actor has received unauthorized access to information or networks, they are able to damage an organization and its networks. They may steal files and data, compromise other users' accounts using privilege escalation. All those eventualities bring inherent risks, costs, and capacity fines to the business — however the long-time period of harm from unauthorized access can carry with it the damaged reputation and trust.
Recent Common Vulnerabilities and Exposures (CVE)
Common Vulnerabilities and Exposures (CVE) is a database that contains a list of vulnerabilities disclosed publicly. CVE number uniquely identifies a vulnerability from the list.
CVE-2022-21582:
This vulnerability allows low-privileged users in the network to access and compromise Oracle Banking Trade Finance via HTTP. It requires human interaction other than a malicious actor. If the attack is successful it results in unauthorized access, creation modification of data, and deletion. this vulnerability can cause partial Denial of Service (DOS)attacks
CVE-2021-37270:
CMS Enterprise website construction system 5.0 has unauthorized access vulnerabilities, Malicious actors use this vulnerability to directly access the specified background path to obtain administrative access without logging into the background path
CVE-2021-34700:
The Cisco SD-WAN vManage Software allows the authentication of malicious actors to read unauthenticated files on the affected system via the CLI interface. This vulnerability ceases to exist because having access to sensitive information is not managed effectively. Exploiting this vulnerability and gaining access to sensitive information allows for the creation of forged authentication requests and gaining access to web UI.
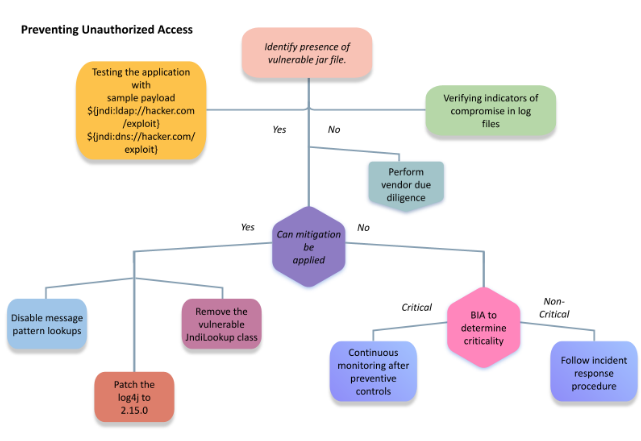
7 Ways to Prevent Unauthorized Access
1. Using the strong password policy
Standardize password length and characters. A strong password must be at least 8 characters and should contain numbers, symbols, and lower- and upper-case letters.
2. Keeping the patches up to date
Providing periodical security patches for the vulnerability in the software or Operating system, drivers, etc., will prevent the malicious actor from using the vulnerability to gain access to the system and steal your data.
3. Implementing Two Factor Authentication and Multi-Factor Authentication (MFA)
Implementing Two Factor and Multi-factor authentication methods are more secure since they require more information to validate the user and grant access to the system.
4. Monitoring user's activity
Monitoring user activity makes it easy to find unauthorized users who accessed sensitive information.
5. Encryption of data and Network system
Encryption is a method that converts data into an unreadable format, using various encryption algorithms and networks also need to be encrypted while communicating inside the networks, so the unauthenticated user cannot access the resources and communication and keeps data safe.
6. Implementing the least privilege to users
Giving access to specific user accounts, who are legit to access the activities like computing processes.
7. Endpoint security
Endpoint security protects the computer assets in the network from cyberattacks and blocks applications which are unsafe or unauthorized through the application control.
CD Bytes!
Managing security Access for every user is necessary for every organization. An effective process and the right tools protect against vulnerabilities and security threats while reducing risk, ensuring compliance, and preventing catastrophic data loss.
Cloud Destinations assess, detect, and mitigate potential vulnerabilities exploitable by hackers. Thereby reducing the threat landscape and keeping the attack surface as small as possible by setting up a routine vulnerability assessment as per your needs for various compliance programs such as PCI, HIPAA, and ISO 27001.
Please reach out to info@clouddestinations.com for any business-related queries.
 Back
Back












 Linkedin
Linkedin








